Course Introduction
Why Study Networks?
- Understand how the Internet works.
- Many development positions rely on networks, including web and mobile development.
- Understand security issues in a networked world.
- Be able to write programs that take advantage of the Internet.
The Internet
While there are many ways that networks could be designed, any many ways that they have been designed in the past, we will look specifically at the design of the Internet.
The Internet is an interconnected set of computer networks spanning the globe, which runs applications including the world wide web, email, games, file sharing, and other communication applications.
The Internet evolved out of early developments in network technology by ARPA, which later changed its name to DARPA. This network, called the ARPANET was first developed in the late 60's. Many of the core concepts of the Internet, including packet switching, the internet protocol, and the TCP protocol were developed for ARPANET.
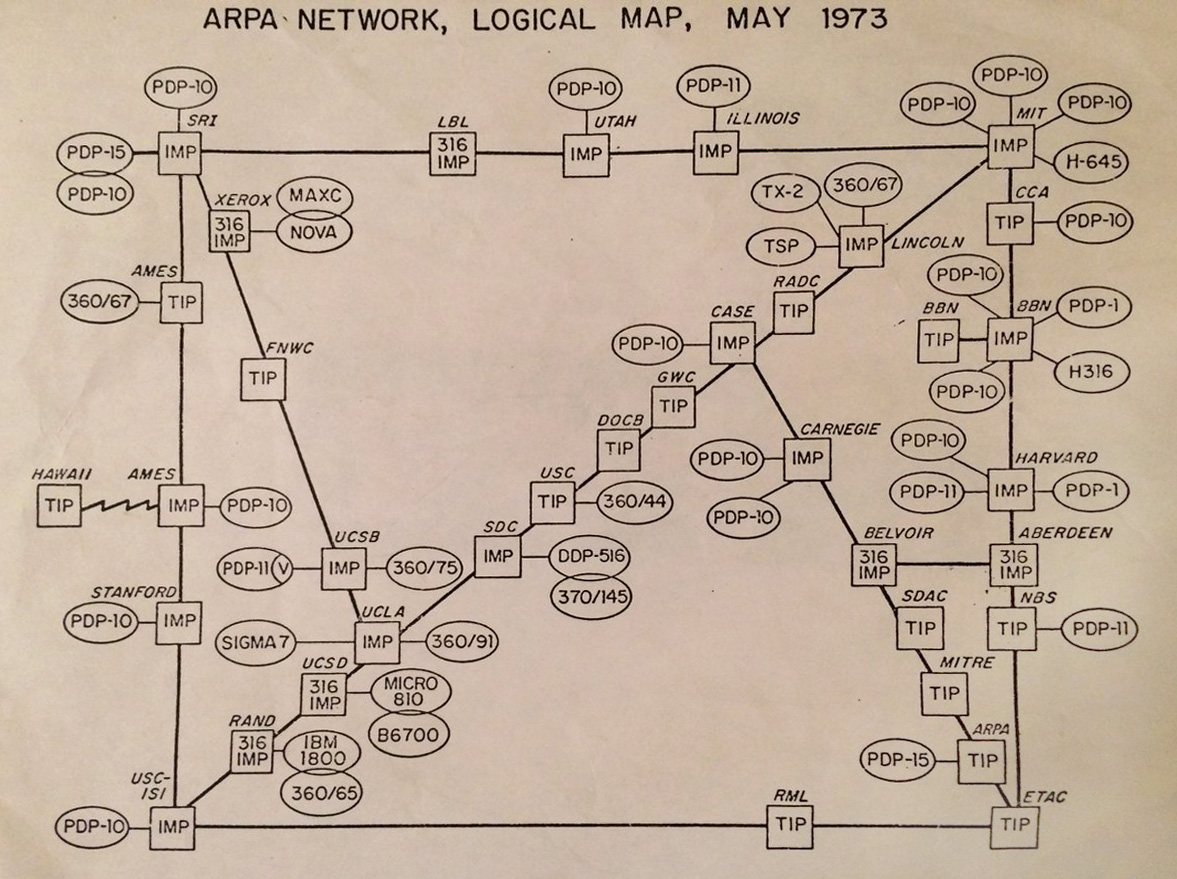
Map of ARPANET (from Wikipedia)
In 1990, ARPANET was decommissioned and the ideas were incorporated into the development of the Internet by several corporations and government agencies.
The Internet is largely decentralized with no single entity controlling its usage. Individual networks are allowed to connect to the Internet and set their own policies. There are two exceptions to this, however. The Internet Corporation for Assigned Names and Numbers (ICANN) is responsible for allocating IP addresses and domain names to participants. The Internet Engineering Task Force (IETF) is responsible for maintaining the standards and protocols which underlay the operation of the Internet.
Packet Switching
The first networks developed, including telegraph networks and the phone network, used circuit switching to support multiple communication. Suppose we have a network, and two sets of parties who wish to communicate:
In circuit switching, dedicated paths are created for the parties. The path, or circuit, is maintained for the entirety of the communication. The relays in the network do not need to multi-task, they are dedicated to one channel of communication:
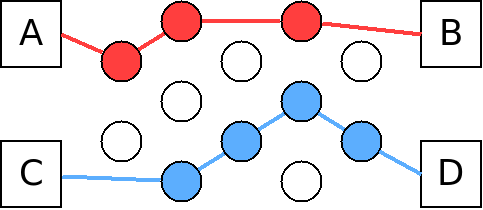
Circuit switching is still used for landline telephone networks, and older wireless network technology (2G and 3G wireless networks).
The Internet, instead was developed using packet switching. In packet switching, communication is broken down into units called packets. The packets are then sent across the network individually. The packets can be put through the network following different paths. Switches in the network can pass along packets from different senders and destined for different recipients:
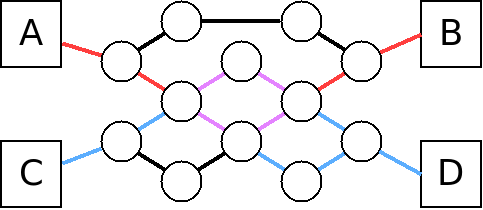
Packet switching is used for the Internet, for VOIP phone systems, and for newer wireless networks.
Circuit switching has the advantage that, once a circuit is acquired for communication, it can take place with minimal latency and error. However, packet switching has a few important benefits which has led to its adoption:
- You can never be out of circuits. The network slows down with increased traffic, but never shuts out new connections.
- A circuit which doesn't transmit much data is wasteful, packet switching makes more efficient use of resources.
- Packet switching is robust to errors. If a packet is lost, it can be resent. The network can reroute to avoid blocked paths. If part of a circuit goes down, there is no recovery.
We will spend a lot of time talking about packets - what goes into them and how they are delivered.
Protocols
The most core idea when discussing networks is the protocol. A protocol is the set of rules governing an interaction between two or more parties.
Protocols exist between people. For instance, in most classrooms there is a protocol when a student has a question, something like the following:
- The student with a question raises their hand.
- The instructor calls on the student, inviting them to ask the question.
- The student asks their question.
- The instructor then answers the question back to the student.
If one party doesn't follow the protocol, then communication breaks down. For example, if the student yells out questions while the instructor is speaking, or if the instructor never calls on students, it won't work properly.
Protocols also exist when computers communicate, over a network. The difference is that computers must be precise and rigorous. Humans can tolerate imprecision but computers can't. Good protocols consider every contingency and specify what both parties should do in each case.
An example protocol is HTTP, the Hypertext Transfer Protocol which describes the communication between web browsers and web servers when dealing with web content. HTTP defines many operations, the most common is the GET operation, which would proceed as follows:
- The browser sends the text "GET" followed by the name of the file they wish to receive.
- The server sends the text "HTTP/1.0" followed by a status code, such as 200 for success, 404 for file not found, 403 for forbidden, etc.
- The server sends various metadata about the file, such as the character encoding, and date.
- The server sends the file contents.
Much of this class will be spent discussing protocols, including existing protocols like HTTP, and the creation of new protocols to solve different problems.
The Layered Model
The Internet was not created as one monolithic entity. Instead, it was created as a layered system, where each layer has one specific problem to solve. One way of describing the layers is the following:
The Physical Layer
Provides the actual transport of bits along some medium, such as Ethernet, Bluetooth or WiFi. Deals with raw streams of bytes instead of logical packets.
The Link Layer
Deals with the delivery of data between different nodes in a local network, and breaking the data stream into "frames". Provides error detection on top of the physical layer, so it can correct problems with the transmission.
The Network Layer
Responsible for routing packets from host to host. In this layer, routers and machines are given addresses, and individual packets are sent from their source to their destination.
The Transport Layer
Provides complete transmission of data from one point to another. Adds packet ordering, resubmission of lost packets, and flow control.
The Application Layer
Protocols and services particular for particular applications. For instance HTTP for the web, SMTP/IMAP for email, SSH, etc.
One major benefit of this layered approach is that it provides modularity. One particular layer can be substituted without impacting the others. For instance, the development of WiFi in place of wired connections only affects the physical layer - the layers above do not need to be changed.
Some layers have one de facto standard protocol - like IP at the network layer, while others have multiple approaches - like TCP vs. UDP at the transport layer.
It also provides encapsulation, each layer is handled independently in software. At each layer, information is added to or removed from packets:
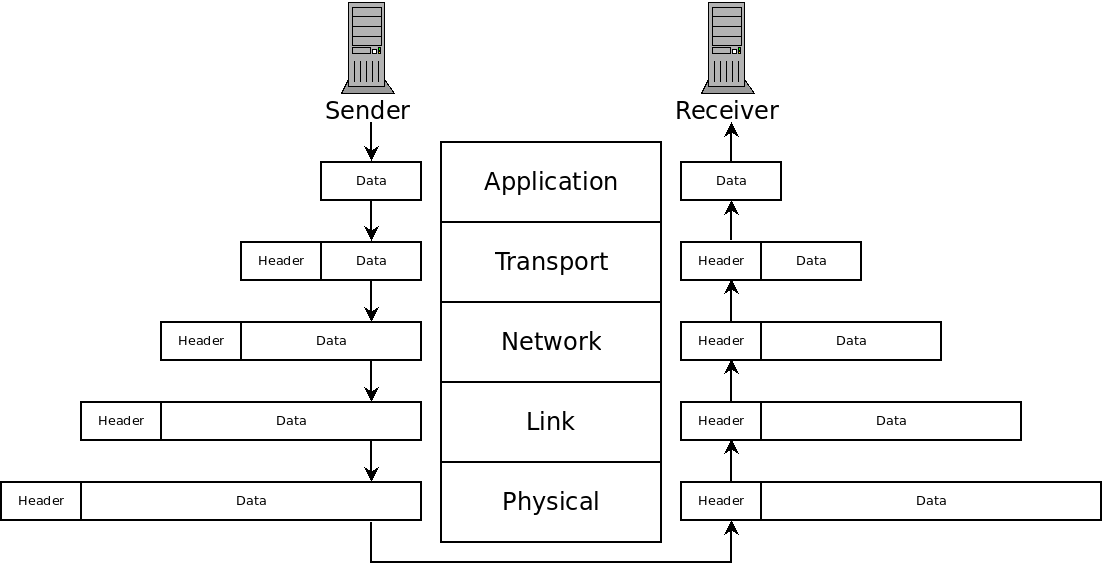
This diagram depicts a packet being sent from one machine to another. The application of the sender specifies some data to be sent, header information is added at each layer of the network stack, until the data is physically sent across to the receiver. At that point, it goes up the network stack of that machine. At each point, the header information is removed for the layer above it, until the original data is given to the application.
We will study the issues and protocols at each layer to get an understanding of how they work and the trade-offs involved.
When Things Go Wrong
We will also look at how the layers of Internet deal with different kinds of errors, such as the following:
- Delays in the network
- Dropped packets
- Network Congestion
- Broken routes
- Machines running at different speeds
In addition to these natural issues that arise in networking, we will look at "man-made" issues that arise from people using the Internet with bad motives such as:
- Spreading malware
- Denial of service attacks
- Packet sniffing
- Address spoofing
What We'll Do
- Learn the core protocols of the Internet.
- Work with existing application-level protocols.
- Develop new protocols.
- Analyze protocols.
- Create Virtual Machines on the Google Cloud.
- Write network code using Python (using existing protocols and creating our own).
What we Won't Do
- Physically connect or configure routers.
- Learn all the details of networking packages e.g. Cisco.