Lab 4: TShark Link Layer
Objective
To use TShark to investigate some aspects of the Link Layer. This lab will ask you some questions. You should turn in your answers over email (either in the message body or in a separate document).
Part 1: MAC Addresses
TShark can display some of the fields in an Ethernet frame for us. Recall that Ethernet frames look like this:
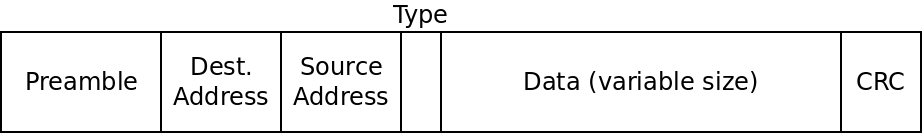
The first thing we will investigate is the address fields. Recall that the address refer to the hardware address of your network interface, not an IP address. These are called HW addresses, Ethernet addresses or MAC addresses.
To find your MAC address, you can use the ip a command,
which prints information on network interfaces:
$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens4: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1460 qdisc fq_codel state UP group default qlen 1000
link/ether 42:01:0a:8e:00:03 brd ff:ff:ff:ff:ff:ff
inet 10.142.0.3/32 scope global dynamic ens4
valid_lft 80374sec preferred_lft 80374sec
inet6 fe80::4001:aff:fe8e:3/64 scope link
valid_lft forever preferred_lft forever
There is a lot of information here. The command shows that we have two interfaces. The one called "lo" can be ignored. That is our "loopback" interface and only connects programs running on this same machine together (some programs use this network to exchange messages).
The "ens4" interface (which may have a slightly different name on your machine) is the main network interface. The MAC address is labelled as "link/ether". In the example above, it's "42:01:0a:8e:00:03".
By default, TShark does not print MAC addresses. To get it to, we can pass the following flags to TShark:
tshark -T fields -e eth.src -e eth.dst
This will cause TShark to print the source and destination MAC address of the packets it sees.
Question 1: Run TShark with the above flags, and also "-c 100" to capture 100 packets. Out of these 100 packets, how many are from your VM, and how many are to your VM? How many different nodes is your VM communicating with? Explain why that number makes sense.
Part 2: Network Type
The type field in the Ethernet frame diagram above is always
included in the frames. One function it has is to distinguish between
IPv4 and IPv6. For IPv4, the type field is equal to 0x800.
For IPv6, it should be 0x86dd
To see the type field, we can run:
tshark -T fields -e eth.type
Use TShark to capture 100 packets again, this time displaying the type field.
Question 2: Is the traffic using IPv4, IPv6, or a mix of both?
Part 3: CRC Checksums
We can look for packets with a bad checksum by passing the "eth.fcs_bad" field:
tshark -T fields -e eth.fcs_bad
If there are any frames with a bad checksum, they should print something out. Frames with a correct checksum will print nothing.
Question 3: Running this for 100 frames, are there any with a bad checksum?
We can also compute CRC32 checksums for any data we want to. To do so, first install the package "libarchive-zip-perl":
sudo apt install libarchive-zip-perl
Then, download this small text file:
wget http://ianfinlayson.net/class/cpsc414/labs/sample.txt
To compute the CRC32 checksum for the data in this file, you can use the following command:
crc32 sample.txt
This will print the 4 byte checksum as 8 hexadecimal digits.
Question 4: What is the checksum value for the sample.txt file?
Next, we'll simulate a change of 1 bit in the data. To do this, open the sample.txt file and change a "b" to a "c". This will change 1 bit of the data because b is ASCII value 98 and c is ASCII value 99. In binary those values are "1100010" and "1100011", so 1 bit different.
Question 5: What is the checksum value now? Did the 1 bit make a small difference in the value or a big one?
Lastly, download two more files:
wget http://ianfinlayson.net/class/cpsc414/labs/file1.txt wget http://ianfinlayson.net/class/cpsc414/labs/file2.txt
Question 6: What are the CRC32 checksums for these two files? What does this mean?
Submitting
When you're finished, email your answers to ifinlay@umw.edu.